How to monitor extractor usage
With the standard authorizations that we propose a user using the extractor has access to all data. As a system administrator you may want to restrict the access to certain tables only. This can be by granting access to certain authorization groups only. However, it can happen that certain tables that are needed for an analysis and those that you want to restrict are part of the same authorization group. In this case you can monitor the activity of the user to validate that only allowed tables are accessed.
To setup monitoring use transaction SM19. Click on the page icon to create a new audit profile.
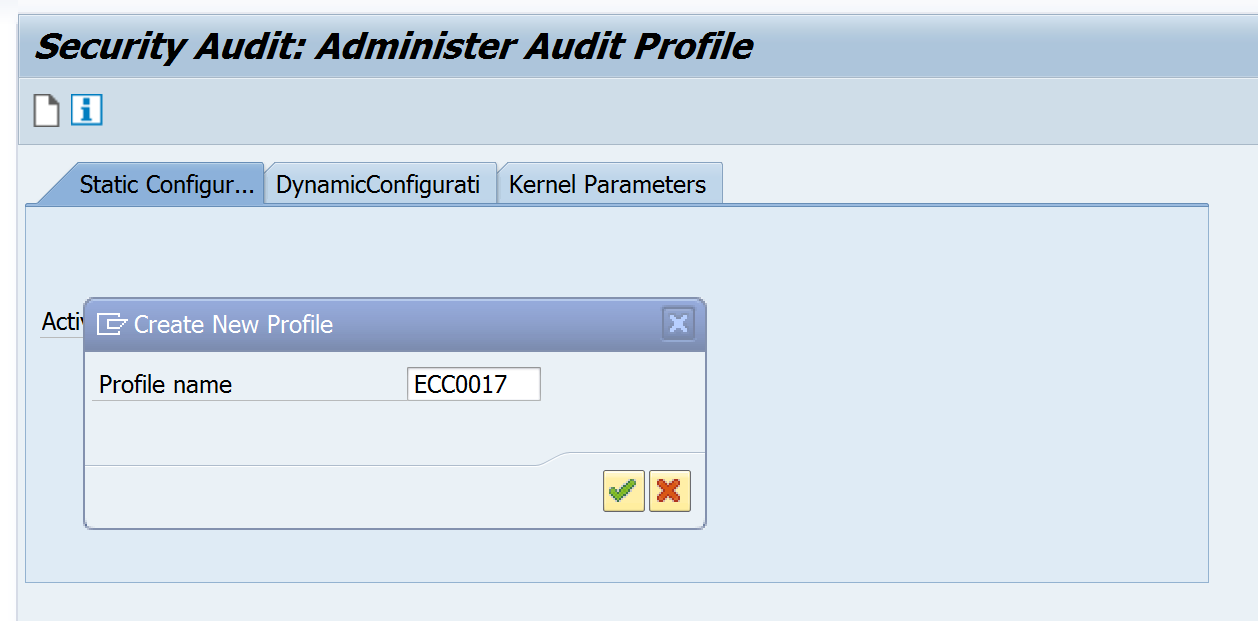
SAP will ask you to provide a name for the new audit profile. Here we give it the same name as the user we will be monitoring. For audit purposes it is advised to create a separate dialog user for extraction purposes so that it does not get mixed with the usage of a standard user.
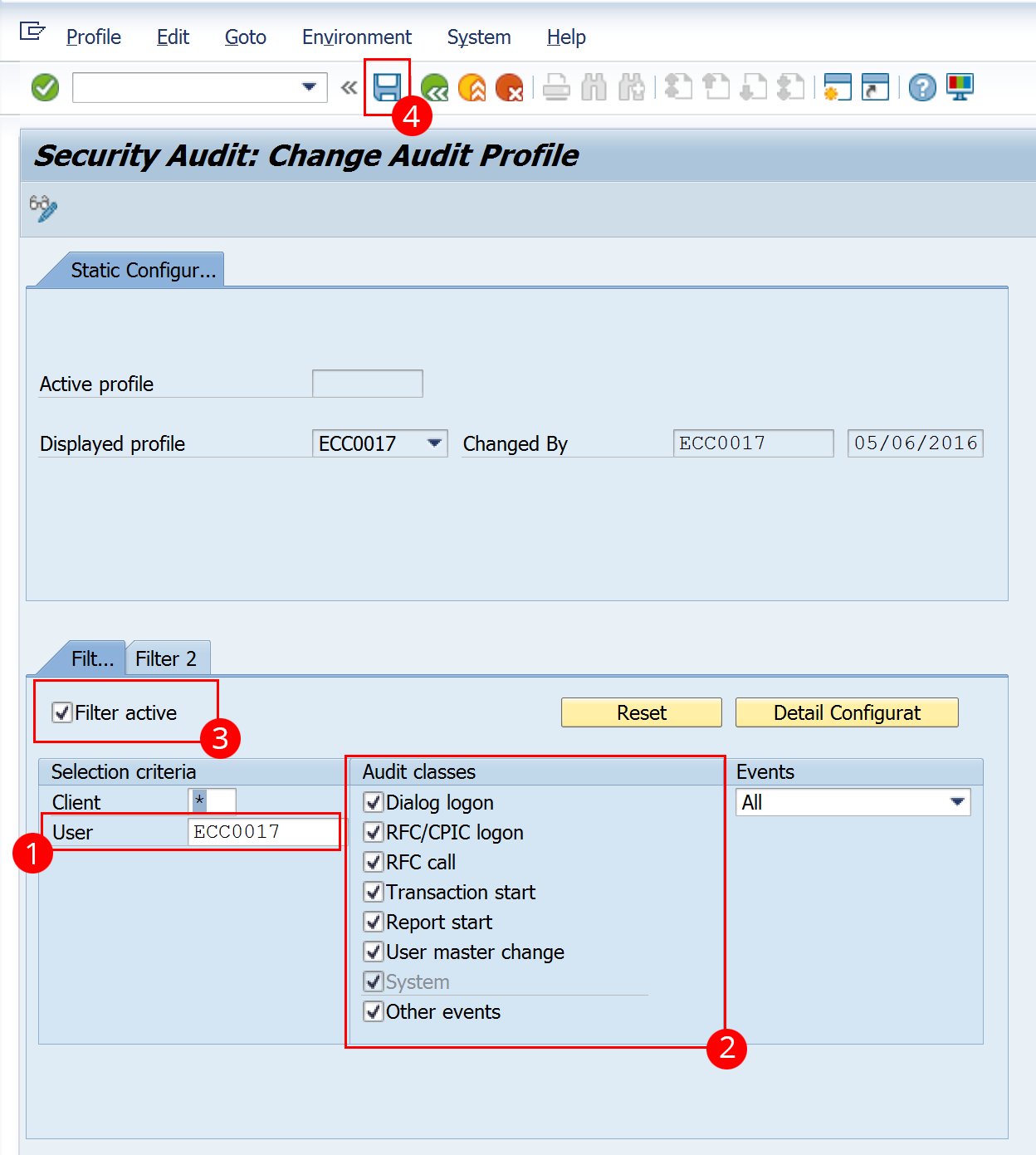
Now you need to enter the user you want to monitor. In our case ECC0017. Select all audit classes to track all activity. In theory it is sufficient to monitor RFC calls only but the login might be abused to do other activities in the system. Click on ‘filter active’ to activate the monitoring.
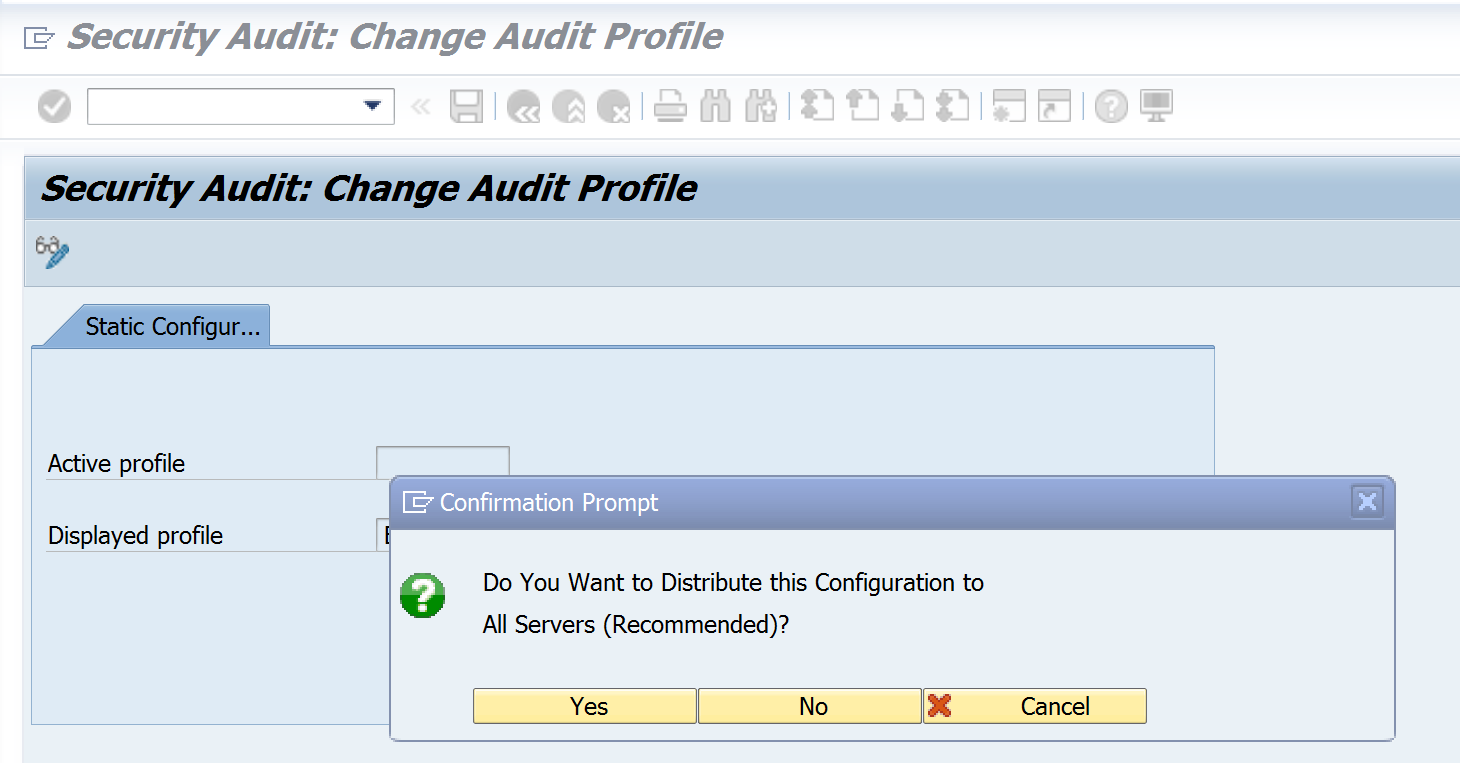
When SAP prompts the question to distribute the configuration to all servers press ‘yes’. SAP keeps the logs for each server separately. So when you have a distributed system you need to make sure that you are logging on all servers in order to capture all activity.
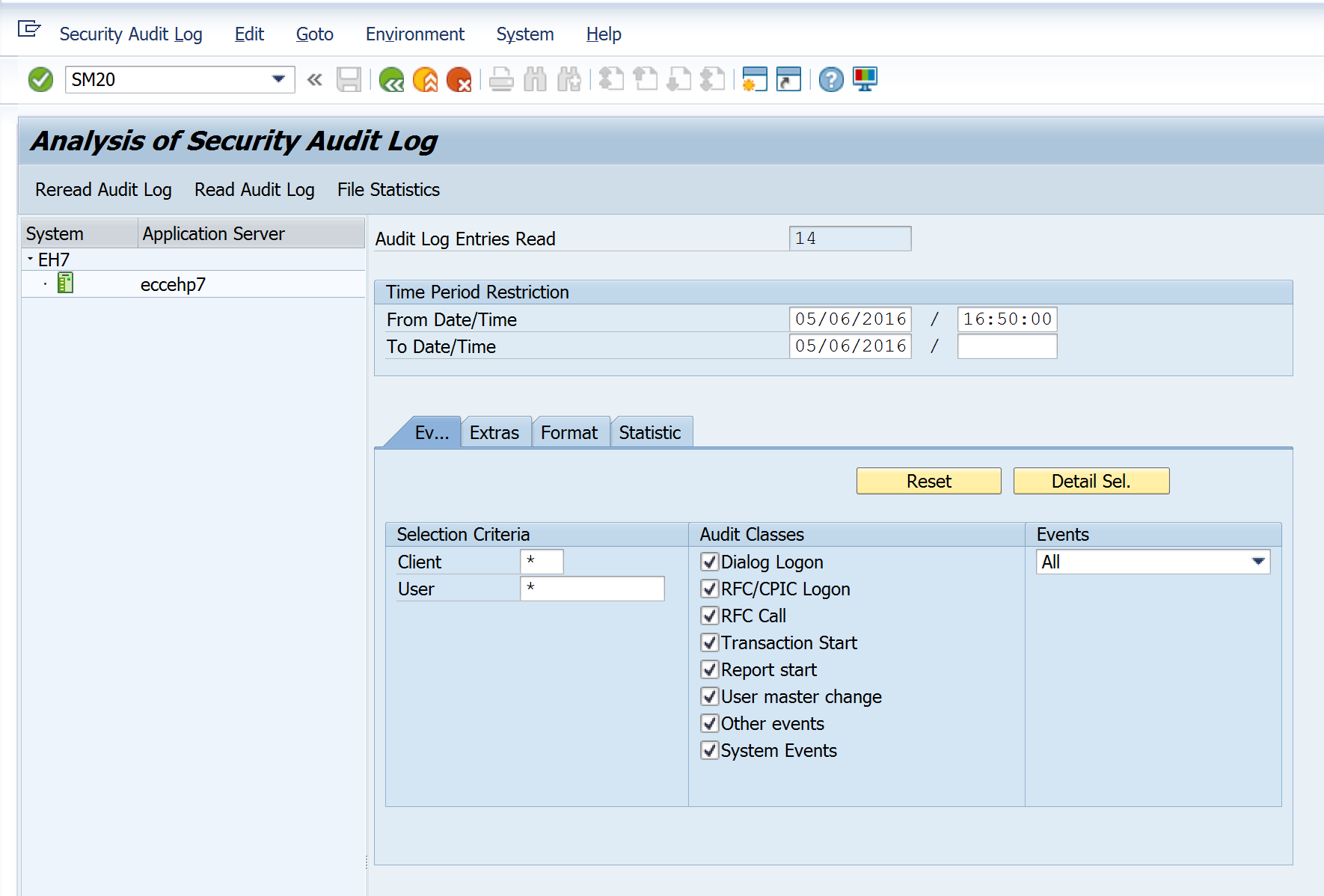
To check the activity of the user use transaction code SM20 (analysis of security audit log). Enter the date range you want to investigate and the user. Click on ‘reread audit log’ to list the activity.
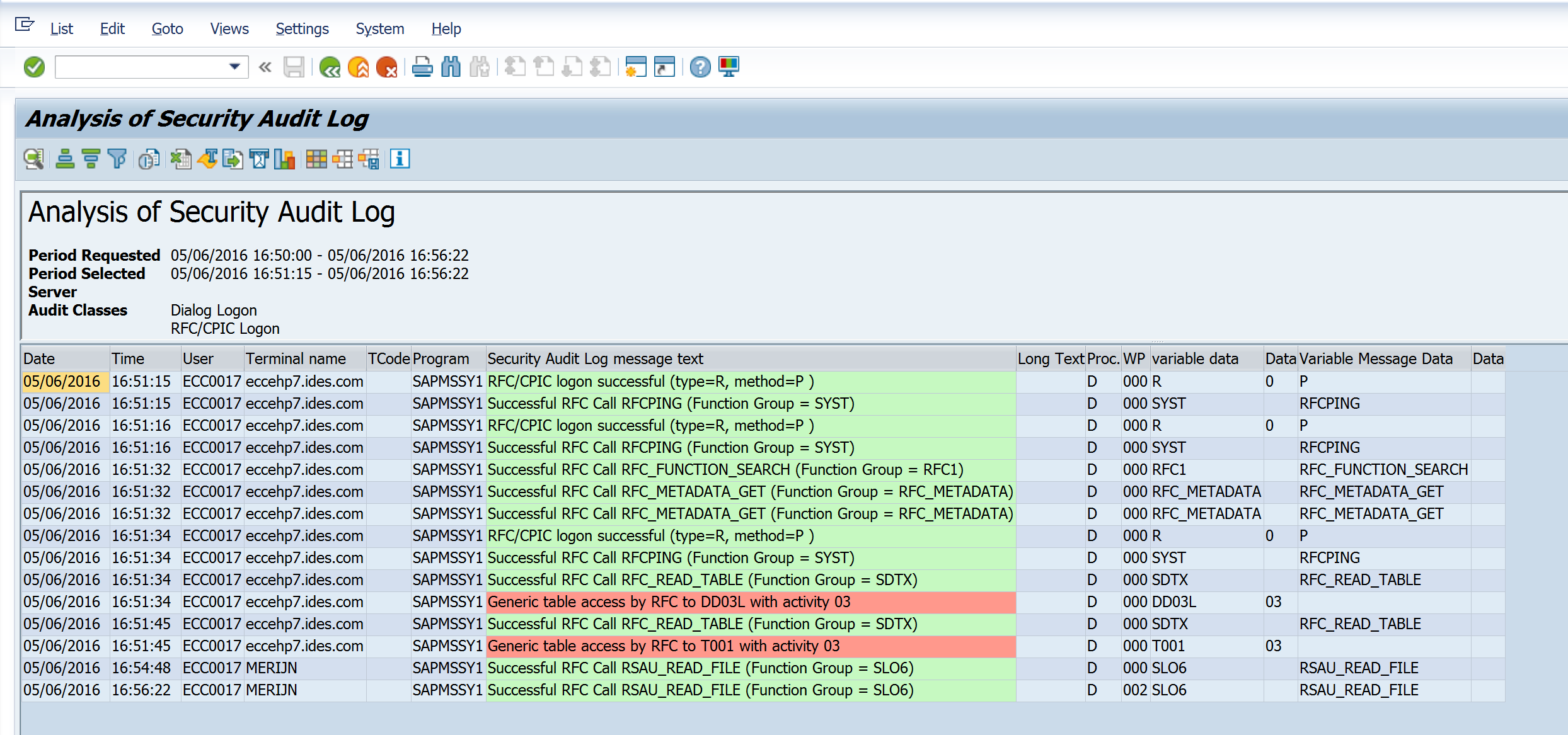
You will get an overview of all the calls made by the extractor to the system. In the example below you see all the actions taken by the program to download table T001. First there is a logon to the system. Next a download of table D003L to know the technical characteristics of table T001 and finally the download of table T001 itself. Note that the activity is 03 meaning display only. The extractor will only copy data from the system. It will never alter any data.